Use of wireless technologies in automation technology is increasing year by year. Users benefit from this, as wireless solutions offer a higher degree of mobility and flexibility. Often it is the cost saving from the elimination of cable installation for the use of a wireless system. The automation industry focuses mainly on wireless technologies, which can be used practically worldwide and function in license-free frequency bands. Thanks to the large bandwidth of 83MHz, a high data throughput and/or the parallel operation of multiple wireless systems in the 2.4 GHz ISM band is possible.
As information is transmitted through the unprotected air, security strategies have to prevent the unauthorized access. With the widely distributed wireless technologies Bluetooth and Wireless LAN, the problem is that the communication interface is accessible for everyone, i.e. every available Bluetooth or WLAN wireless product fundamentally permits a connection with the industrially employed network. The potential danger is especially high with the WLAN interface, since it extremely common in the PC environment and very vulnerable to hacker attacks. Thanks to the closed technology of an industrial wireless path with Trusted Wireless 2.0. In principle, it is much better protected against possible attacks. Moreover, the frequency hopping method makes spying on the protocol much harder. But, Trusted Wireless 2.0 also has two genuine security mechanisms, an encryption of all transmitted information in accordance with the Advanced Encryption Standard (AES), as well as a user data integrity check described in accordance with RFC3610.
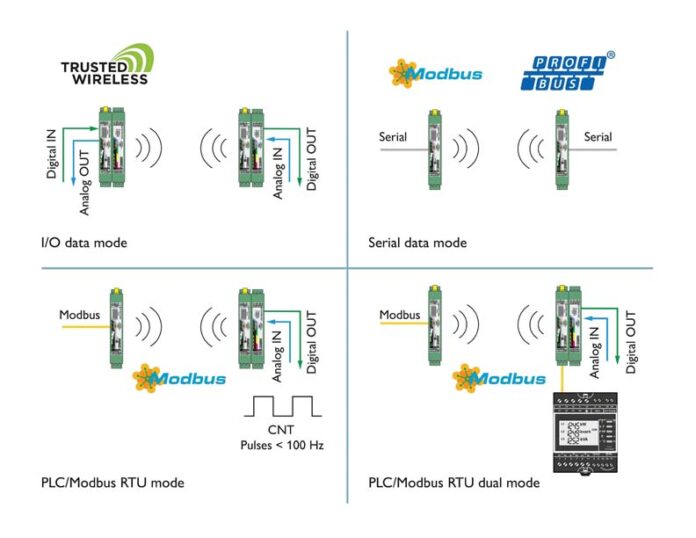
Areas of application for Trusted Wireless 2.0
Trusted Wireless 2.0 is a wireless technology developed specially for industrial use. It is particularly suitable for sensor-actuator information covering cable infrastructure. It is used in small to medium-sized data quantities, over larger distances of hundreds of meters to several kilometres. Trusted Wireless 2.0 is characterized by its particularly good adaptability to the desired industrial application and offers a high degree of reliability, robustness, safety and flexibility.
The main features of Trusted Wireless 2.0 are:
- Robust communication thanks to FHSS (Frequency Hopping Spread Spectrum)
- Automatic and manual coexistence mechanisms
- Secure communication due to encryption (AES 128 Bit) and integrity check
- Long range thanks to high receiver sensitivity and variable data transmission rates
- Flexible networks with automatic connection management
- Distributed network maintenance makes things easier and faster
- Extensive diagnostic properties
- Adaptability to the desired application.
More information: E-mail- adverts@phoenixcontact.co.in, Website:www.phoenixcontact.co.in



















